Hotels Targeted by fake Booking.com style Malware Scam
What Hospitality Teams Need to Know — and How to Reduce Risk
Cybercriminals are increasingly targeting the hospitality sector, using realistic-looking emails and websites that impersonate trusted booking platforms like Booking.com.
At Geod, we’re aware of a rise in attacks that don’t rely on technical hacking, instead, they rely on tricking staff into taking actions that compromise hotel systems.
One of the latest examples is a malware technique known as ClickFix, and it’s particularly effective against hotel environments.
How This Attack Works (non-technical version)
This attack is designed to look routine, something hotel teams deal with every day.
Typical attack flow:
A hotel staff member receives an email appearing to come from a fake Booking.com email, often about a cancellation, payment issue, or guest complaint.
The email creates urgency and prompts the recipient to click a link
The link leads to a fake website that closely resembles a legitimate booking platform
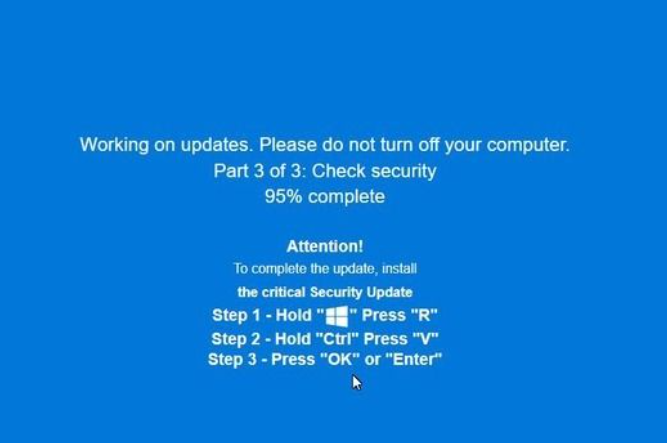
4. The site displays a fake system error or crash message often styled to look like a Microsoft Windows alert
5. The user is instructed to “fix” the issue by following steps on screen. This may involve pressing keys or pasting commands into the system
6. By following these steps, the user unknowingly installs malware themselves
Once installed, the attacker may gain access to:
Login credentials
Hotel systems
Reservation platforms
Internal networks
Why Hotels Are Being Targeted
Hotels are attractive targets because:
Staff regularly handle bookings, cancellations, and payment queries
Fast-paced environments encourage quick responses
Shared computers and accounts are common
Front-desk and reservations teams are customer-focused, not security-focused
Attackers design these scams specifically to blend into normal hotel workflows.
Why Traditional Security Tools Aren’t Enough
What makes this attack particularly dangerous is that:
No software vulnerability is exploited
Antivirus may not immediately block it
The malware is executed by a real user following instructions
This is why staff awareness and layered security controls are critical.
Summary & Recommendations
This campaign highlights a growing trend in cyber attacks against the hospitality sector.
criminals are not just exploiting technology, they are exploiting people.
By impersonating trusted booking platforms and using realistic system messages, attackers can trick hotel staff into installing malware themselves, often without triggering traditional security tools.
GEOD Recommendations for the hospitality sector.
To reduce risk, GEOD recommends that hospitality organisations:
Train staff regularly to recognise suspicious booking-related emails and fake system alerts
Encourage verification, especially for urgent or unexpected requests (e.g call a known number to verify)
Restrict user permissions to prevent unauthorised commands or software from running
Monitor endpoints for unusual behaviour and respond quickly to anomalies
Cybersecurity in hotels is not just an IT concern. It is an operational risk that affects guest data, reservations, and business continuity.
George O’Dowd
Head of IT Advisor | Founder, GEOD Consulting
George works with growing businesses as a Head of IT on a part-time basis, providing senior oversight, cyber risk insight, and clear decision-making — without the cost or commitment of a full-time hire.
With over 20 years’ experience and a background building and exiting a leading IT and cybersecurity firm, George brings practical, commercial judgement to technology decisions that matter.